Case: AWS S3 Bucket Permissions - Access Denied
I am trying to give myself permission to download existing files in an S3 bucket. I've modified the Bucket Policy, as follows: My understanding is that addition to the policy should give me full rights to "bucketname" for my account "myuid", including all files that are already in that bucket. However, I'm still getting Access Denied errors when I try to download any of those files via the link that comes up in the console.
Why My S3 Access Denied (403 Forbidden Errors)
Some users found that their Amazon S3 is returning the 403 Access Denied error when trying to access objects in my Amazon Simple Storage Service (Amazon S3) bucket. For example, you are downloading or uploading files to S3 and get an access denied error.
Here are several reasons about getting "Access Denied" (403) errors when trying to access Amazon S3 (Simple Storage Service):
● Incorrect permissions.
● Issues with bucket policies and ACLs.
● Incorrect object paths or bucket names.
● AWS Signature Version mismatch.
● Expired temporary credentials.
● CORS configuration problems.
● Object encryption settings.
● Network or connectivity issues.
● Incorrect request signing.
● AWS region mismatch.
● AWS service outages or maintenance.
How to Fix S3 Access Denied Error | Common Solutions
How to troubleshoot your AWS S3 access denied error? Please refer to the following common methods when you can't connect to s3 service access denied.
Check Bucket Policies and IAM Policies
Check the storage bucket policy and any related IAM user policies for access denial statements. Verify that requests to the storage bucket meet any conditions listed in the storage bucket policy or IAM policy. Ensure that there are no incorrect denial statements, missing operations, or incorrect formatting in the policy.
1. Log in to your AWS Management Console, then open the Amazon S3 console at https://console.aws.amazon.com/s3/.
2. In the left navigation pane, choose Buckets. From the Buckets list, choose the name of the bucket that you want to view or edit a bucket policy for.
3. Choose the Permissions tab.
4. Review the bucket policy for statements with "Action": "s3:GetObject" or "Action": "s3:*".
5. (Optional) Modify the bucket policy. For example, you can remove or edit statements that block public read access to s3:GetObject.
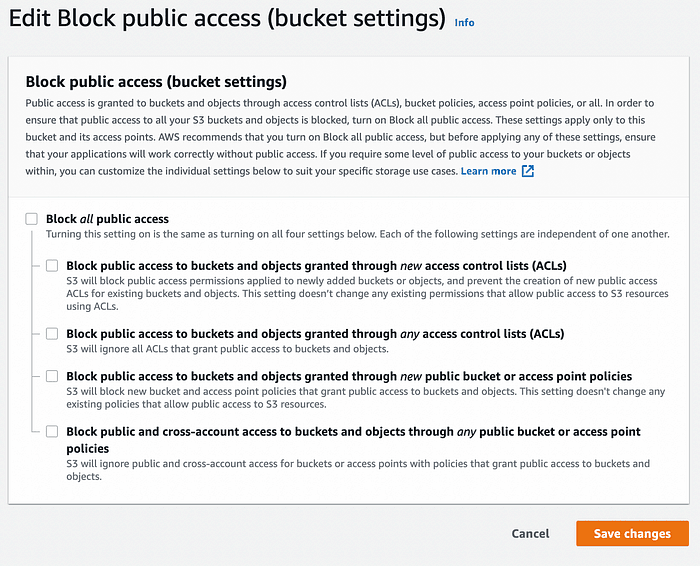
S3 Block Public Access Settings
If your request fails due to public access or policies, check S3's Block Public Access settings for your account, bucket, or access point. Since April 2023, new buckets have these settings enabled by default. When set to TRUE, they act as explicit deny policies, overriding ACLs, bucket policies, and IAM user policies. To confirm if Block Public Access is causing rejections:
1. Log in to your AWS Management Console using your credentials.
2. Choose the S3 bucket for which you want to adjust the Block Public Access settings.
3. Inside the bucket's dashboard, locate the "Permissions" tab or section.
4. Find the "Block Public Access" settings. These settings allow you to control public access to the bucket and its contents.
5. Click on the "Edit" to modify the Block Public Access settings.
You'll typically see a set of options that allow you to block public access on different levels. These could include:
6. After adjusting the settings to your desired level of public access restriction, save your changes.
It's good practice to periodically audit and review your S3 bucket's access settings to make sure they remain aligned with your security policies.
Confirm Object Ownership
By default, S3 objects are owned by the AWS account that uploaded them, regardless of the bucket's ownership. If other accounts can upload objects to your bucket, verify the ownership of the objects that your users are unable to access.
Note: When encountering errors with AWS CLI commands, ensure you're using the latest version of the AWS CLI.
Confirm the account that owns the objects
1. Use the list-buckets AWS Command Line Interface (AWS CLI) command to obtain your account's Amazon S3 canonical ID by querying the Owner ID.
2. Run the list-objects command to acquire the Amazon S3 canonical ID of the object's owner. Replace DOC-EXAMPLE-BUCKET with your bucket's name and exampleprefix with the prefix value.
Tip: Use the list-objects command to check several objects.
3. If the canonical IDs don't match, the object isn't owned by you. The object's owner can grant you full control by using the put-object-acl command. Replace DOC-EXAMPLE-BUCKET with your bucket's name and exampleobject.jpg with the key name.
4. After the object's ACL is changed to bucket-owner-full-control, the bucket owner can access the object. However, this ACL change doesn't alter object ownership. To change ownership, the bucket's account can use the cp command to copy the object onto itself.
If you can’t connect to s3 service access denied, you could try to check bucket policies, modify the object ownership, etc.
✎ Automatically Backup Your Data to Amazon S3
For a dependable and secure backup solution for your virtual machines, SQL Server databases, or Windows PCs/Servers, AOMEI Cyber Backup stands out as a robust software choice. This powerful backup tool provides a centralized solution, streamlining the backup and recovery process, ensuring reliability, and enhancing overall data security. More »
Conclusion
Encountering "Access Denied" (403) errors when trying to access Amazon S3 can be attributed to a variety of factors. These range from misconfigured permissions, bucket policies, and access control settings to issues with object paths, authentication mechanisms, and network connectivity. Addressing these errors requires a careful review of permissions, configurations, and settings, coupled with accurate handling of credentials and requests.
This article guides you to troubleshoot AWS S3 Access Denied error. Maintaining an understanding of these potential pitfalls and implementing the appropriate solutions will enable smoother and more secure interactions with Amazon S3